Beware of emails claiming to be from Microsoft
Page 1 of 1 • Share
 Beware of emails claiming to be from Microsoft
Beware of emails claiming to be from Microsoft
Fake Windows update installs ransomware on PCs
Most readers of this site will recognize a malicious email when they see one, but they’re a source of danger to less tech-savvy individuals. One such campaign claims to be from Microsoft, advising people to update Windows, but doing so will install ransomware on a computer.
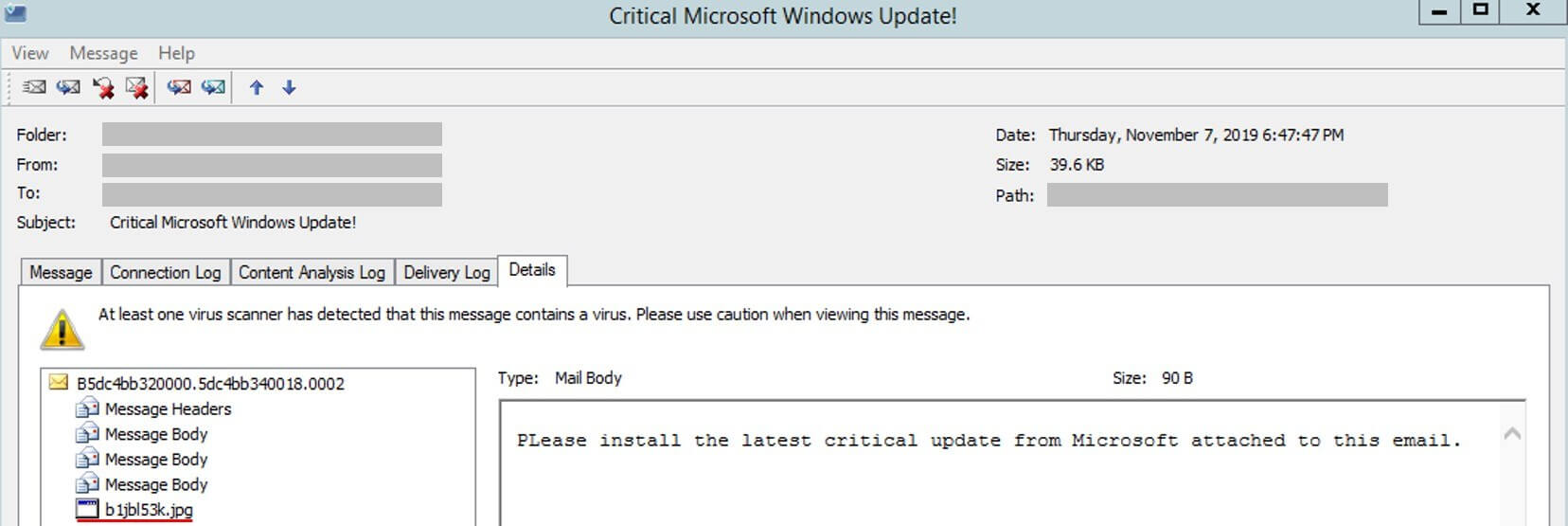
Researchers from Trustwave’s SpiderLabs discovered the spam emails, which come with an 'Install Latest Microsoft Windows Update now!' or 'Critical Microsoft Windows Update!’ subject line. Microsoft, of course, doesn’t send out Windows updates through email.
The messages contain just one sentence, and the first word begins with two capital letters, making it appear even less legitimate. Recipients are asked to click an attachment to download the ‘update.’ While the file has a .jpg extension, it’s actually an executable .NET downloader that delivers malware to the infected system.
Clicking on the file will download another executable, this one called bitcoingenerator.exe from a (now-removed) Github account named misterbtc2020. Like the email attachment, this is .NET compiled malware—the Cyborg ransomware.
As with other ransomware, bitcoingenerator.exe encrypts users’ files and changes their extension to its own: 777. The ransomware also leaves a copy of itself called ‘bot.exe’ hidden at the root of the infected drive.
Victims will then find a ransom note named "Cyborg_DECRYPT.txt" on their desktop, which demands $500 to decrypt the files.
When the researchers looked for the ransomware’s original filename, they found three other samples and discovered that a builder for the ransomware exists. There was even a YouTube video containing a link to the builder hosted in Github, which had two repositories: one with the ransomware builder binaries, the other with a link to the Russian version of the builder.
Ransomware has become criminals’ malware of choice in recent times, especially when it comes to hitting local government systems. On Monday, Louisiana was targeted for the second time this year, though its cybersecurity team stopped the attack before any damage was done.
Most readers of this site will recognize a malicious email when they see one, but they’re a source of danger to less tech-savvy individuals. One such campaign claims to be from Microsoft, advising people to update Windows, but doing so will install ransomware on a computer.
Researchers from Trustwave’s SpiderLabs discovered the spam emails, which come with an 'Install Latest Microsoft Windows Update now!' or 'Critical Microsoft Windows Update!’ subject line. Microsoft, of course, doesn’t send out Windows updates through email.
The messages contain just one sentence, and the first word begins with two capital letters, making it appear even less legitimate. Recipients are asked to click an attachment to download the ‘update.’ While the file has a .jpg extension, it’s actually an executable .NET downloader that delivers malware to the infected system.

Clicking on the file will download another executable, this one called bitcoingenerator.exe from a (now-removed) Github account named misterbtc2020. Like the email attachment, this is .NET compiled malware—the Cyborg ransomware.
As with other ransomware, bitcoingenerator.exe encrypts users’ files and changes their extension to its own: 777. The ransomware also leaves a copy of itself called ‘bot.exe’ hidden at the root of the infected drive.
Victims will then find a ransom note named "Cyborg_DECRYPT.txt" on their desktop, which demands $500 to decrypt the files.
When the researchers looked for the ransomware’s original filename, they found three other samples and discovered that a builder for the ransomware exists. There was even a YouTube video containing a link to the builder hosted in Github, which had two repositories: one with the ransomware builder binaries, the other with a link to the Russian version of the builder.
Ransomware has become criminals’ malware of choice in recent times, especially when it comes to hitting local government systems. On Monday, Louisiana was targeted for the second time this year, though its cybersecurity team stopped the attack before any damage was done.
_________________


8DonCo
 Re: Beware of emails claiming to be from Microsoft
Re: Beware of emails claiming to be from Microsoft
Just delete the email , DO NOT Click to update
_________________


8DonCo
 Similar topics
Similar topics» Beware....
» Beware of Airport Scam!
» FDA to Purell: Stop claiming your hand sanitizers eliminate Ebola
» Microsoft takes down Vietnamese group behind 750 million fake accounts
» Microsoft lost "phone war"
» Beware of Airport Scam!
» FDA to Purell: Stop claiming your hand sanitizers eliminate Ebola
» Microsoft takes down Vietnamese group behind 750 million fake accounts
» Microsoft lost "phone war"
Page 1 of 1
Permissions in this forum:
You cannot reply to topics in this forum
 Home
Home